How to Set Up OWASP ZAP and FoxyProxy on MacOS

Note: This tutorial was written in 2017.
An http proxy is an important item in the hacker’s toolbox. It sits between your browser and the web server, something like this:
browser <---> http proxy <---> server
Why is this useful? Well, setting up an http proxy allows you to capture all of the responses coming from the server so that you can dissect them later, looking for ways in which the server might be vulnerable. It also lets you modify outgoing requests in order to execute attacks, or just to send the same request over and over in a repeat attack.
If you’ve never set up an http proxy before, it can be a little confusing. In this post I will walk you through the process. We will use OWASP Zed Attack Proxy (ZAP) as our http proxy and connect it to our browser with the FoxyProxy extension. My guide will center around Mac OS X and Chrome because that’s what I happen to use myself.
Throughout this guide you will be prompted to enter your password a lot. This is expected. Whenever prompted, simply enter your password and proceed.
Installing and setting up ZAP
You will need Java 7+ in order to run ZAP, which you can download and install here.
Once you have installed the latest Java, go to the official ZAP download page and download the latest version of ZAP for your operating system. Once the download completes, run the installer and open ZAP. You should be greeted with a page that looks like this, asking if you want to persist the ZAP Session:
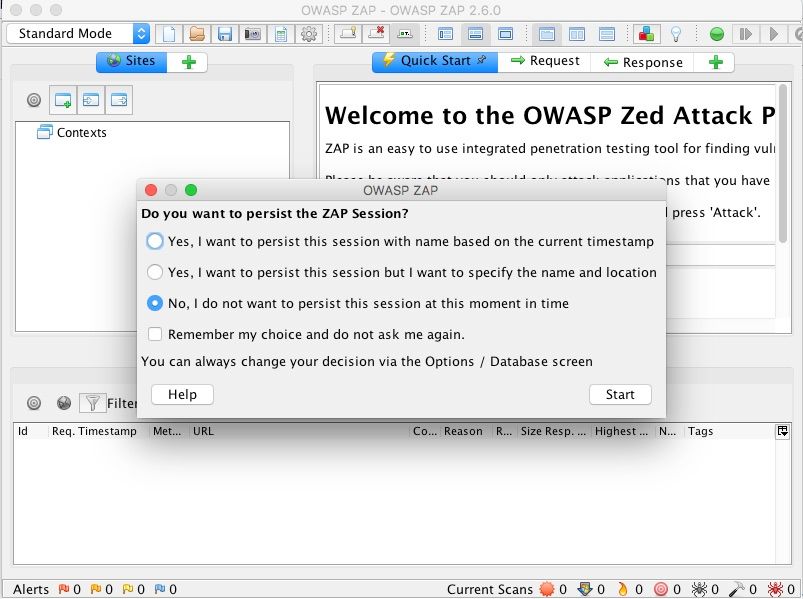
Select no for the time being (as we’re just trying to set the app and poke around) and hit “Start”.
Now that you have successfully installed ZAP, let’s go ahead and configure it to act as a proxy for our local web traffic. In the system menu bar, click ZAP > Preferences to open the options menu. From there, select on Local Proxy and enter 127.0.0.1 as the address and 8080 as the port.
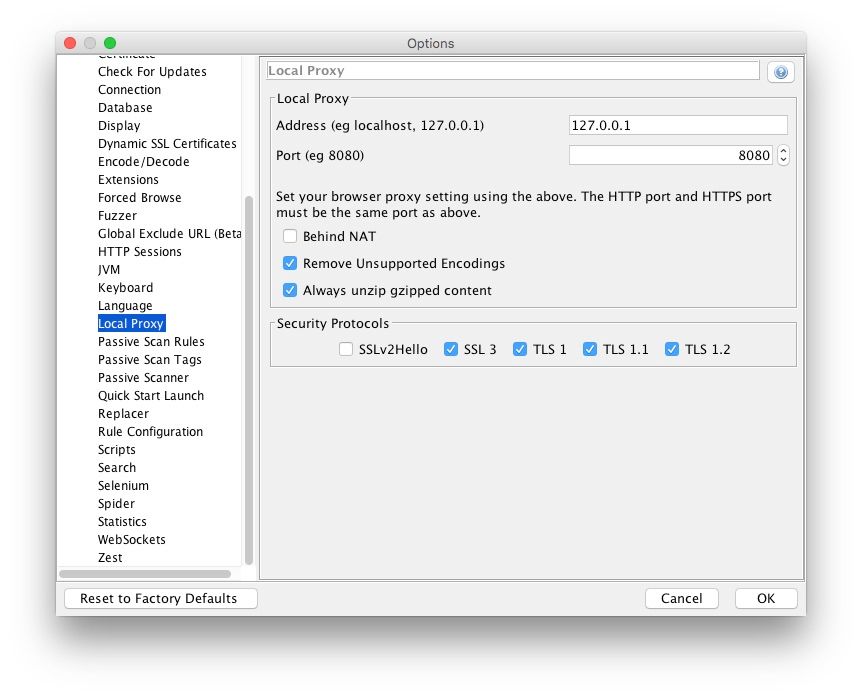
This configures ZAP to run locally at https://127.0.0.1:8080.
Add the ZAP certificate to your system’s trusted certificates
Next, we need to tell our system to trust messages forwarded to us by the ZAP proxy so that we will be able to visit urls that start with https://. To do this, we need to give the Operating System the ZAP proxy’s certificate.
Without leaving the Options menu, click Dynamic SSL Certificates on the sidebar, then click Save. Put the owasp_zap_root_ca.cer certificate file somewhere where you will remember it. I chose to put it in ~/workspace/zap/ but anywhere is fine. Once this is done, click OK to close the Options menu.
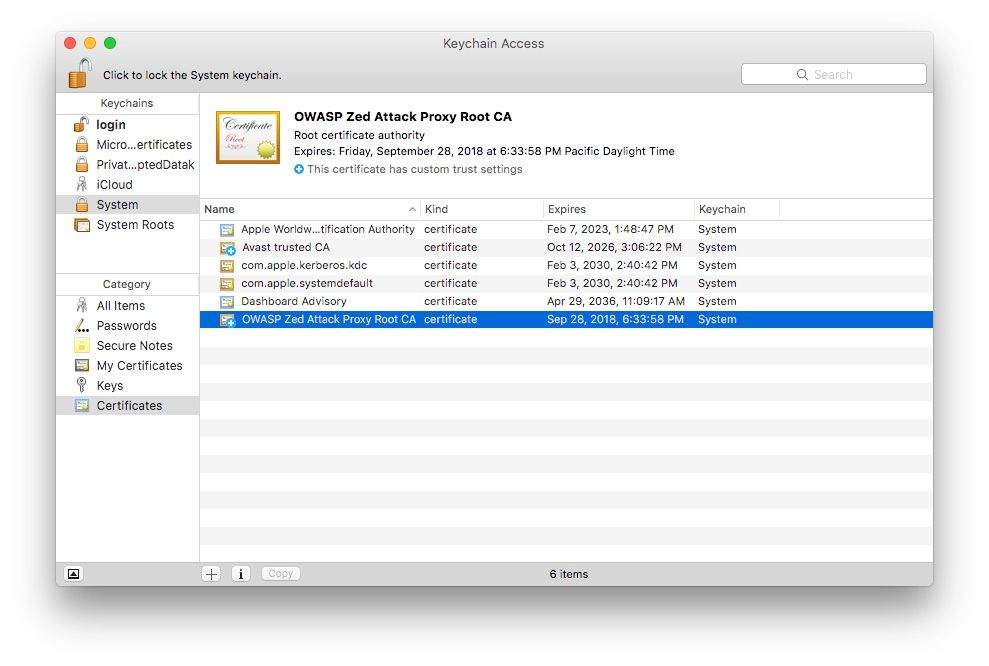
Next, use Spotlight to open the Keychain Access system utility. It should look something like this:
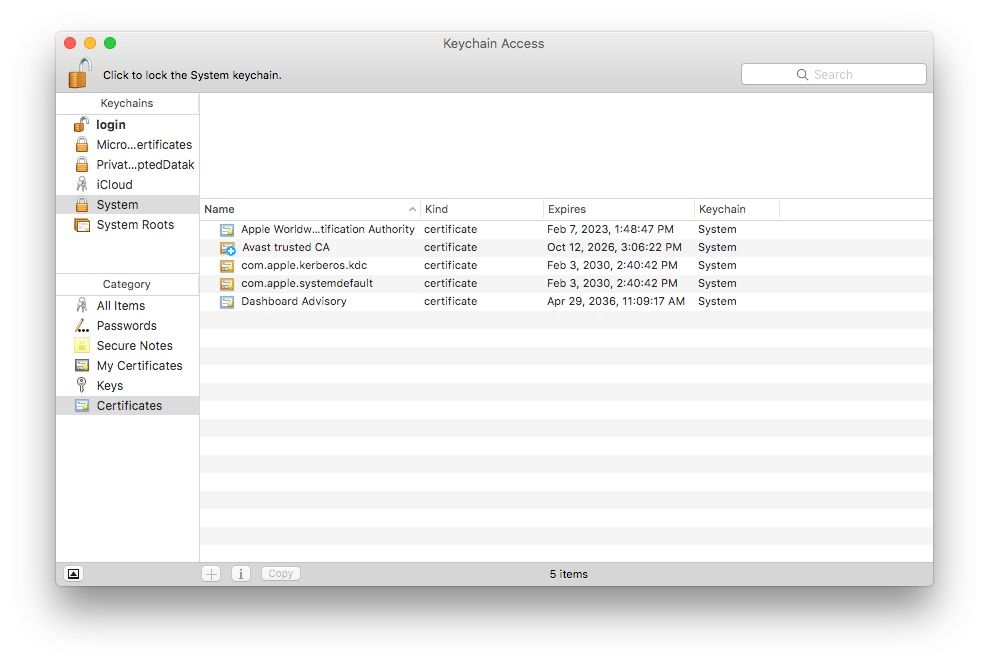
In the Keychains sidebar, select System. In the Category sidebar, select Certificates
Alright, now we’re ready to actually import the certificate! Click File > Import Items and go find the .cer file you saved earlier. It should appear in your list of certificates with a little red x on it indicating it is still not trusted.
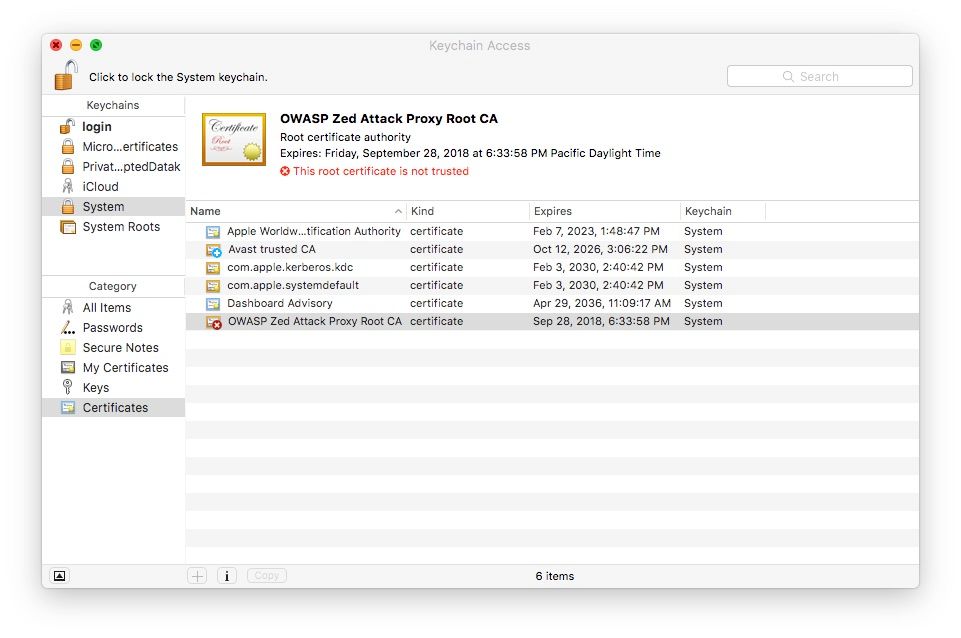
Double click the certificate and in the Trust menu that appears, change the Secure Sockets Layer (SSL) setting to Always Trust.
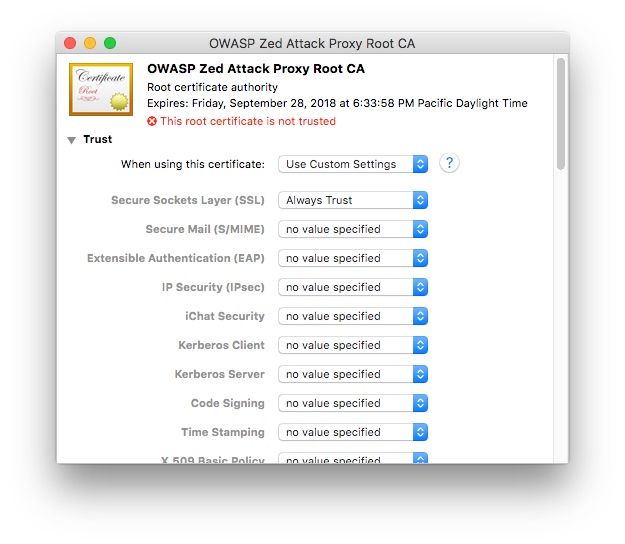
Close this menu and you should see that the little red x has turned into a blue cross, indicating that the certificate now has custom trust settings.
Install the FoxyProxy extension and configure it to point to your ZAP proxy
Install the FoxyProxy extension on Chrome or Firefox. All of the following instructions will be for Chrome users but Firefox users should be able to do basically the same thing.
FoxyProxy allows you to choose which websites you want to access through the proxy. Going through a proxy will noticeably slow down network requests, so you probably only want to pass traffic to the sites you’re analyzing through it. However, if you do want to go through the proxy for all sites you visit, FoxyProxy allows you to configure that as well.
Click the FoxyProxy icon in your menu bar and choose Options. This will take you to a screen where you can configure your proxies.
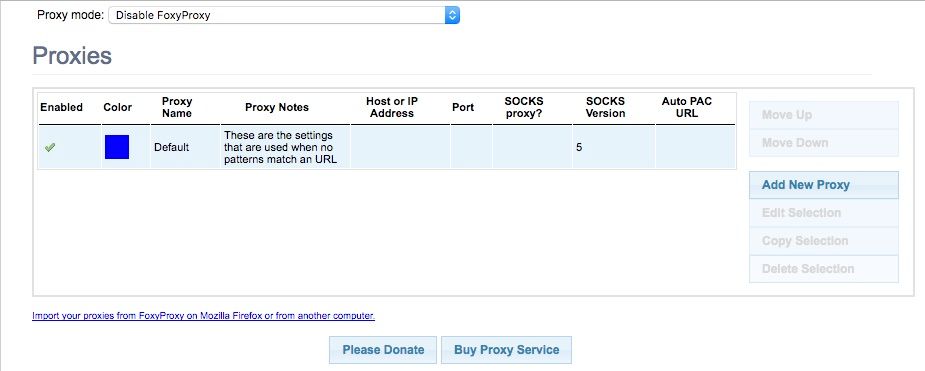
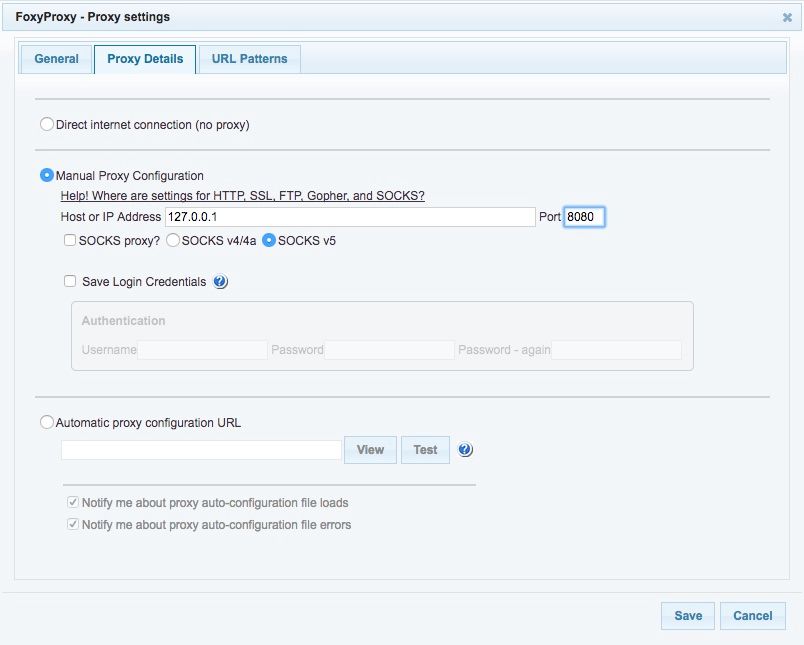
Now we’re going to tell FoxyProxy how to talk to the ZAP Proxy server we set up previously. Select Add New Proxy. Under Proxy Details, select Manual Proxy Configuration and enter 127.0.0.1 as the Host or IP Address and 8080 as the Port.
Next, we want to tell the extension what sites we want to send through the proxy. Click URL Patterns on the top bar and then select Add new pattern. Give your pattern a name and enter the wildcard pattern for one of the sites you want to analyze. For example, if I wanted to send all traffic to and from Google through the proxy, this is what I would enter:
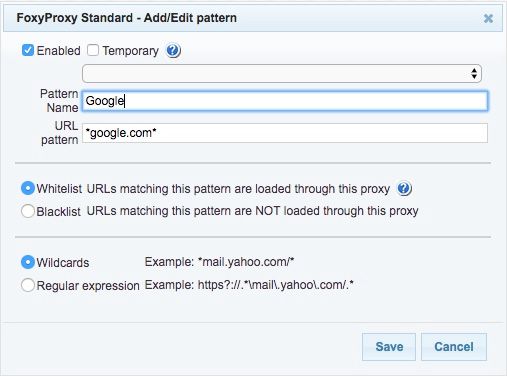
Hit Save. Feel free to add more patterns if you have multiple sites you want to analyze, but it may be wise to just do one site at first and then test out whether it’s working.
If you want to you can click the General tab up top and give this proxy a name. Either way, when you’re done, hit Save.
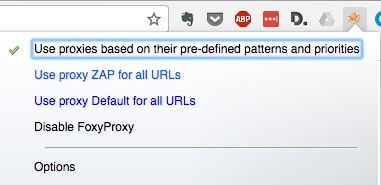
With your proxy rule now created, you can activate your new rule by clicking the FoxyProxy icon in the Chrome menu and choosing Use proxies based on their pre-defined patterns and priorities.
If everything went according to plan, your traffic to the websites you specified will now be routed through your proxy on the way to your browser. You can test this out by navigating to the site you told FoxyProxy to send through the proxy. Once the page loads, go back to the ZAP window. All of the requests and responses made in order to load the page should show up in the History section.
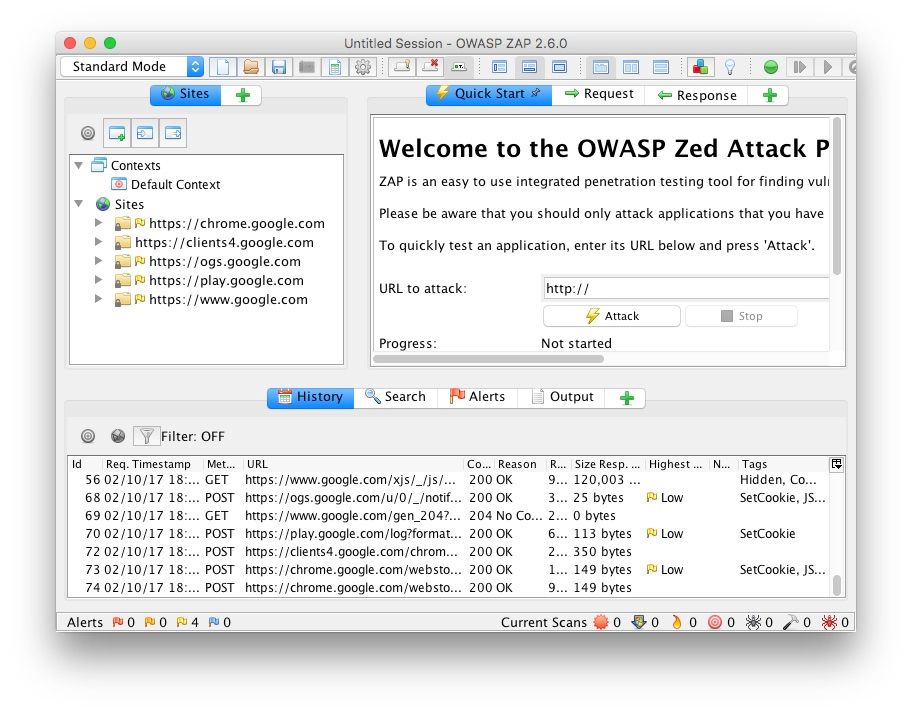
You did it! Now you can use ZAP to your heart’s content to analyze and pen test your site! If you would like to stop proxying, simply close the ZAP app and click Disable FoxyProxy in the FoxyProxy extension settings
Note: DO NOT use this to attack sites that you haven’t been expressly given permission to attack.